的 CCNI实验室 is not just a research facility; it's an innovation hub where brilliant minds unite to address pressing challenges in computational science and cybersecurity. 通过前沿研究, 动手实验, and collaborations with industry and government partners, 我们正在推动技术进步. 探索我们的研究, 认识我们卓越的团队, 加入我们,共同塑造一个更加安全的, 聪明的, 相互联系的世界.
选定研究项目
Energy Efficient Beamforming Optimization for 5G mmWave Networks
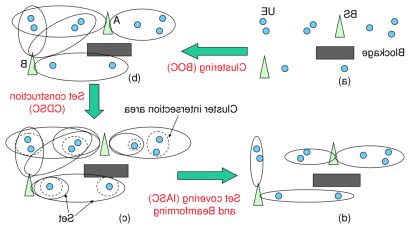
的 毫米波 (mmWave) frequency band is a promising candidate for next generation cellular and wireless networks. To compensate the significantly higher path loss due to the higher frequency, the mmWave band usually uses the beamforming technology. 然而, this makes the network topology control a great challenge. We propose a novel framework for network topology control in mmWave networks, termed 面向波束成形的拓扑控制 (好处). 的 objective is to reduce total transmit power of base stations and interference between beams. BOON smartly groups nearby user equipment into clusters, 从用户设备集群构造集合, and associates user equipment to base stations and beams. BOON平均只使用10%, 32%, and 25% transmit power of three state-of-the-art schemes in the literature, 分别, 以达到相同的网络和速率.
User Association and Scheduling for 5G mmWave networks
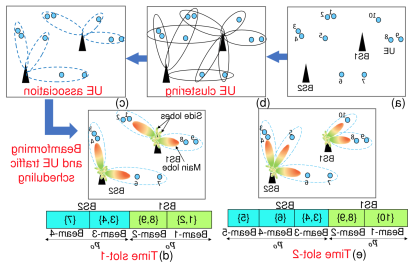
的 毫米波 (mmWave) band offers vast bandwidth and plays a key role for next generation wireless networks. 然而, the mmWave network raises a great challenge for 用户关联和调度, 由于有限的功率预算和波束形成, 不同的用户流量负载, 用户服务质量要求, 等. We propose a novel framework for 用户关联和调度 in multi-base station mmWave networks, 被称为 clustering Based dOwnlink UE assOciation, Scheduling, beamforming with power allocaTion (提高). 的 objective is to reduce the downlink network transmission time, 根据基站电力预算, 波束形成器的数目, 用户流量负载, 用户对服务质量的要求越来越高. 平均, BOOST减少了37%的传输时间, 30%, 和26%, 并实现了56%的和率增益, 43%, 和34%, 分别, compared with three state-of-the-art schemes in the literature.
隐私 is a fundamental challenge for a variety of smart applications that depend on data aggregation and collaborative learning across different entities. We develop a novel privacy-preserved architecture where clients can collaboratively train a deep learning model while preserving the privacy of each client's data. Our main strategy is to carefully partition a deep neural network to two non-colluding parties. One party performs linear computations on encrypted data utilizing a less complex homo- morphic cryptosystem, while the other executes non-polynomial computations in plaintext but in a privacy-preserved manner. Our extensive experiments on different datasets demonstrate not only stable training without accuracy loss, but also 14 to 35 times speedup compared to the state-of-the-art system.
DeepMag
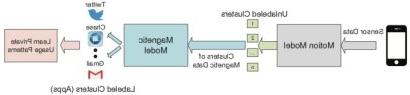
We have discovered a new vulnerability on smartphones due to the malicious use of unsupervised sensor data. We demonstrate that an attacker can train deep Convolutional Neural Networks (CNN) by using magnetometer or orientation data to effectively infer the Apps and their usage information on a smartphone with an accuracy of over 80%. 此外, we show that such attacks can become even worse if sophisticated attackers exploit motion sensors to cluster the magnetometer or orientation data, 将准确度提高到高达98%. 为了减轻这种攻击, we develop a noise injection scheme that can effectively reduce the App sniffing accuracy to only 15% and at the same time has negligible effect on benign Apps.
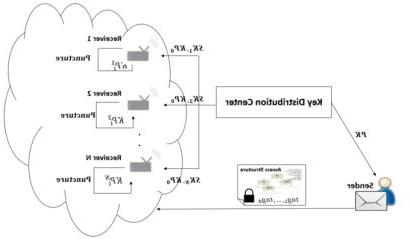
Puncturable Attribute-Based Encryption for Secure Data Delivery in Internet of Things
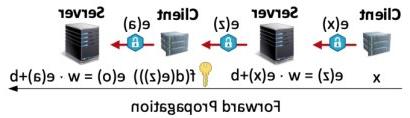
While the Internet of Things (IoT) is embraced as important tools for efficiency and productivity, it is becoming an increasingly attractive target for cybercriminals. We develop practical Puncturable Attribute Based Encryption schemes that are light-weight and applicable in IoTs. 的 attribute-based encryption is adopted for fine grained access control. 的 secret keys are puncturable to revoke the decryption capability for selected messages, 收件人, 或者时间段, thus protecting selected important messages even if the current key is compromised. 与传统的前向加密相比, a distinguishing merit of the developed approach is that the 收件人 can update their keys by themselves without key re-issuing from the key distributor. It does not require frequent communications between IoT devices and the key distribution center, neither does it need deleting components to expunge existing keys to produce a new key. 此外, we devise a novel approach which efficiently integrates attribute-based key and punctured keys such that the key size is roughly the same as that of the original attribute-based encryption. We also implement the proposed scheme on Raspberry Pi and observe that the computation efficiency of the proposed approach is comparable to the original attribute-based encryption. Both encryption and decryption can be completed within tens of milliseconds.
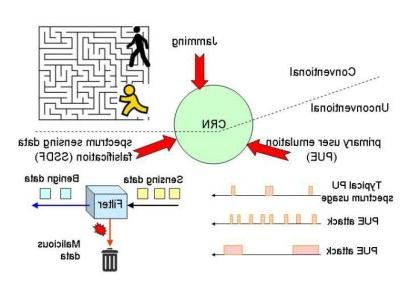
Wireless communications play a key role in both the national economy and our everyday life. 然而, the radio spectrum used by wireless communications is a limited and extremely valuable natural resource, and is being exhausted due to inefficient allocation. This spectrum scarcity problem has motivated the development of the disruptive cognitive radio and spectrum sharing technologies. 的 powerful capability of cognitive radio to reconfigure the waveform, and the dynamic manner of spectrum access raise two new security threats to cognitive radio networks, primary user emulation (PUE) and spectrum sensing data falsification (SSDF). A malicious user can launch PUE attacks to cause denial of service (DoS) to secondary users, such that the network performance is significantly degraded.
协同频谱感知, a fusion node determines the availability of a channel based on sensing data from other nodes. 恶意用户可以发起SSDF攻击.e., sending false sensing data to mislead the fusion node, 这将导致向次要用户发送DoS, 或对主要用户造成有害干扰.
We are designing effective countermeasure algorithms and mechanisms to address the PUE and SSDF attacks to build secure cognitive radio networks.
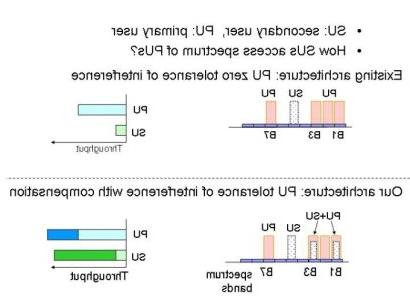
的 existing architecture of cognitive radio networks fails to offer incentives to primary users. 因此, secondary users have to conduct spectrum sensing extensively and behave conservatively, 这会导致很大的开销, 频谱利用率远低于预期. 此外, the existing architecture is vulnerable to the PUE and SSDF attacks. Together, these two issues can reduce the benefit of cognitive radio networks to a marginal level.
Guided by the theories of network coding and dirty paper coding, we are designing new cognitive radio network architectures to incentivize primary users to cooperate with secondary users for spectrum sharing, 并缓解PUE和SSDF的攻击, such that both the performance of both primary users and secondary users are dramatically improved.
此外, capitalizing on the recent evolution of spectrum policies, we am designing a novel architecture termed on-demand spectrum access (ODSA), which eliminates the PUE and SSDF attacks and enables users to securely and efficiently share spectrum.
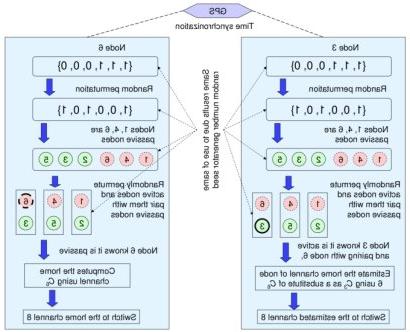
Rendezvous refers to how a transmitter finds the channel of a receiver. 在传统的无线网络中,比如WiFi, 这是一个微不足道的问题, 因为所有节点都在同一个通道上. 然而, it is a totally different story for cognitive radio networks.
在认知无线电网络中, the secondary user or cognitive radio nodes typically operate on different channels due to the dynamic and spatially heterogeneous availability of channels. This situation raises a challenge for MAC Protocols: how do two nodes rendezvous? 许多研究假设使用一个共同的控制通道. 然而, this is vulnerable to jamming and traffic congestion.
We are devising proactive anti-jamming rendezvous algorithms, such that cognitive radio nodes are able to proactively find the peers, 为了达到高效, 轻量级, 和近乎最佳的会合地点.
的 powerful capability of cognitive radio to reconfigure the waveform, and the dynamic manner of spectrum access raise two new security threats to cognitive radio networks, primary user emulation (PUE) and spectrum sensing data falsification (SSDF). A malicious user can launch PUE attacks to cause denial of service (DoS) to secondary users, such that the network performance is significantly degraded.
协同频谱感知, a fusion node determines the availability of a channel based on sensing data from other nodes. 恶意用户可以发起SSDF攻击.e., sending false sensing data to mislead the fusion node, 这将导致向次要用户发送DoS, 或对主要用户造成有害干扰.
We are designing effective countermeasure algorithms and mechanisms to address the PUE and SSDF attacks to build secure cognitive radio networks.
实验地点: 考夫曼大厅232号
实验室的电话: 757-683-3470
CCNI实验室最靠谱的网赌软件报道
ODU awarded $1 million from the National Science Foundation to help support high-achieving students in cybersecurity program.
Backdoor Detection, Mitigation, and Prevention in Deep 学习 Models
国家安全局,2021 - 2023年,共同负责人
A Development and Experimental Environment for 隐私preserving and Secure (DEEPSECURE) Machine 学习 研究
NSF, 2021 - 2024, Co-PI
Blockchain-based Deep 学习 Management to Enable Smart NextG Wireless Networks
CCI, 2022 - 2023, Co-PI
Distributed Online Intrusion Detection System for IoT devices via Power Side-channel Auditing
CCI, 2022 - 2023, Co-PI
5G及以后的波束成形优化
Cci, 2021 - 2022, PI
安全分布式数字化制造
研究中心,2018 - 2019年,副主任
Building a THz Testbed to Expand CCI 5G Testbed for 6G 研究
Cci, 2021 - 2022, PI
Comprehensive Assessment and Diagnostics for Federated AI Algorithms in Cyber Physical Systems
CCI, 2021 - 2022, Co-PI
DeepPOSE: Securing 运输 Systems from GPS Spoofing Attacks
Cci, 2020 - 2021, PI
Deep 学习 Driven 网络安全 研究 in a Multidisciplinary Environment
Nsf, 2019 - 2022, PI
Hampton Roads NROTC Consortium Midshipman Cyber 研究 and Training
ONR, 2020 - 2021, Co-PI
Improving the Success of Low-Income Students in a 网络安全 Program
国家科学基金会,2018 - 2023,主持
A Beamforming Optimization Framework for 大规模毫米波网络
国家科学基金会,2017 - 2019,主持
Nsa, 2021 - 2022, PI
Preparing Tomorrow’s Heroes to Secure the Cyberspace
国家安全局,2019 - 2020,PI
Planning Grant: Engineering 研究 Center for Safe and Secure Artificial Intelligence Solutions (SAIS)
国家安全局,2018 - 2020年,共同负责人
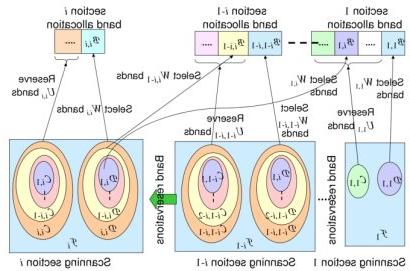
NeTS: 按需频谱接入: Application-Oriented Dynamic Spectrum Access
国家科学基金会,2013 - 2018,主持
net - wn:迈向高性能网状网络
国家科学基金会,2007 - 2010,主持
国家安全局,2021 - 20222,PI
网络安全 研究 in a Multidisciplinary Environment
国家科学基金会,2017 - 2020,主持
Preparing Tomorrow’s Heroes to Secure the Cyberspace
国家安全局,2016 - 2017年,共同负责人
NeTS: Collaborative 研究: 学习 to help: Trading spectrum ownership for performance
国家科学基金会,2010 - 2013,主持
Implementation of Vertically Integrated Curriculum for Cognitive Radio Communications
国家科学基金,2009 - 2011,共同主持